UAG 2010 and AD FS v2 are Better Together
This white paper was published over multiple separate blog posts. This post combines all of them into a single continues document so you can get it all from one source and in correct order. Please leave your comments if you have any questions.
Introduction
Unified Access Gateway (UAG) SP1 has introduced support for the AD FS v2. Now it is possible to publish claims based applications via UAG and provide secure access to AD FS servers by using one of many different configuration topologies supported by these products. This paper explains how to design solution by using UAG and AD FS v2, what type of critical requirements will dictate specific configuration and how to get around some of known limitations. It is assumed that reader has basic knowledge of UAG technology and AD FS technology, as this paper will build on that knowledge and introduce more advanced concepts of UAG and AD FS integration.
There are four main topologies that you can choose for AD FS WebSSO design and they are largely depend on the authentication requirements from the Internet to the UAG server or AD FS server and authentication requirements to the published application. The main topologies are as following:
- Authentication to UAG Portal via Forms Based Authentication and accessing internal claims based applications and other types of applications.
- Authentication to UAG Portal via Certificate Based Authentication (Soft Certificate or Smart Card based certificate) and accessing internal claims based applications and other types of applications.
- Authentication to UAG Portal via Claims Based Authentication and accessing internal claims based applications.
- Authentication to UAG Portal via Claims Based Authentication and accessing internal non claims based applications.
Of course, the WebSSO configuration can be extended to the Federated WebSSO configurations, where customers will be accessing resources published by your company UAG or where your company might require authentication against UAG before accessing resources published by your partner company. The following three topologies are extensions of the last three main topologies:
- Require your company external users to use strong AuthN when they access 3rd party trusted claims based applications. This is an extension of the second topology in the previous list.
- Cloud based authentication or partner based authentication. In this scenario, customers access claims based applications published by UAG server and provide security tokens issued by the Cloud Based Identity Provider or Partner company identity provider to AD FS v2 published by the UAG server. This is an extension of the third topology in the previous list.
- Customers accessing non claims based applications published by UAG server by providing security tokens to AD FS v2 published by the UAG server. This is an extension of the fourth topology in the previous list.
There is another potential design topology which existed before UAG SP1. It is always possible to just publish internal AD FS v2 server via UAG server as a web app and expose authentication against STS Proxy FBA or straight to the actual AD FS server FBA or Certificate based authentication. This type of configuration does not utilize new advanced functionality introduced in UAG SP1 and we are not planning to review it here or use it as potential design topology.
The rest of the document is divided into two parts:
Part 1 – Provides detailed review of each topology. Before looking at potential design choices for potential customer environment we must understand how each topology works, what type requirements it has and any type of limitations.
Part 2 – Provides a sample design of UAG and AD FS solution. Powered by the knowledge of configuration options we’ll look how to fit each topology or a combination of topologies to different customer situations.
Authentication to UAG Portal via Forms Based Authentication and accessing internal claims based applications and other types of applications
Many companies want to provide rich application experience to its remote workforce and telecommuters. This is one of the most common configurations for WebSSO scenario where company needs to publish internal applications to its remote users while ensuring that application access is done via secure access mechanism and users are properly authenticated before accessing internal applications. One of the great advantages of using FBA on the UAG trunk is that it will allow us to access all kind of applications on the back end, as long as you can authenticate to them with the same AD credentials used during FBA. It can be NTLM authentication, it can be Kerberos Constrained Delegation or it even can be forms based authentication, UAG can do them all.
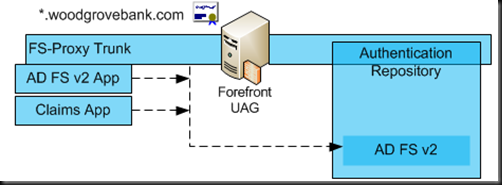
Figure 1 shows classic design with Microsoft Active Directory (AD) acting as main authentication directory and providing access to the internal applications using NTLM or Kerberos authentication and providing authentication to the IDP STS. IDP STS server is published on UAG as an application server and it can be authenticated to just like any other internal Web application.
Figure 1: System Components
With this configuration users authenticate to the UAG portal with their user name and password and then are able to access any type of application via Single Sing On experience. For Kerberos and NTLM based applications it is accomplished via application configuration just like it was done in the prior versions of UAG. For claims based applications, the UAG is configured with additional authentication provider – AD FS v2, which provides SAML security tokens for authenticated users and allows seamless access to the application. Figure 2 shows how two different applications published on the same UAG portal use different authentication providers. As shown, application that uses Windows Authentication is configured with the same authentication provider as the UAG Portal Trunk, so after user is authenticated to the UAG trunk he/she can gain access to the application without providing additional credentials, experiencing SSO.
Figure 2: UAG Trunk Configuration
For the claims based application it works slightly different. The UAG is configured with additional authentication provider pointing to the AD FS v2 server. The claims based application is configured to use this AD FS v2 authentication provider. So how SSO is accomplished in this configuration? After configuring application with AD FS v2 based authentication provider UAG will publish another application under the application list. To accomplish SSO, you’ll need to open that application and under authentication tab configure SSO with the same authentication provider as the main UAG trunk (under which this app is published), in this case it is AD. When user decides to access claims based application, it will first authenticate to the AD FS v2 server by using AD credentials, obtain a security token and then present this token to the application. Figure 3 shows simplified authentication flow to the claims based application via UAG.
Figure 3: Authentication Flow
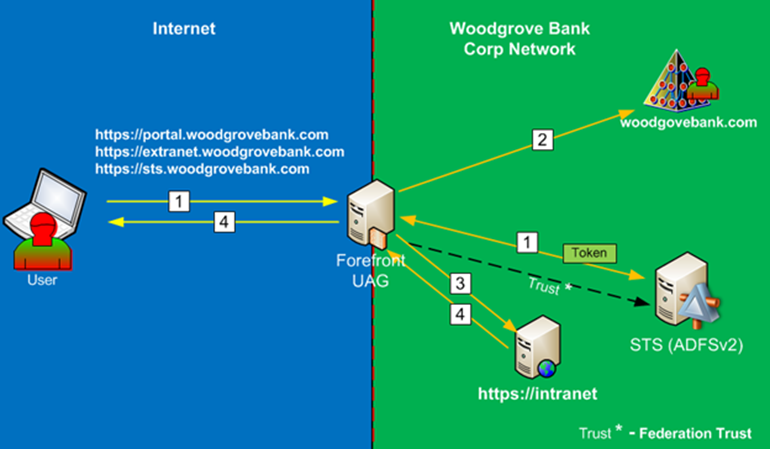
- To access UAG Portal external users will be required to provide Username/password via Forms Based Authentication.
- UAG will authenticate user against Active Directory.
- After authenticating to UAG they will be presented with applications based on their security profile. It will be presented via UAG portal.
- When user tries to access claims based application, the application will redirect the web browser request to the AD FS v2 server for user to obtain a security token.
- Depending on the configuration, the AD FS server might show the home realm discovery page to users on which they must choose the organization to which they belong; in this case, it would be Woodgrove Bank, but since this is a WebSSO configuration, the IDP STS will not show home realm discovery page.
- The IDP STS will send back a HTML 401 response message for user to authenticate. Forefront UAG is able to provide a single sign-on (SSO) experience for the user by answering the 401 response with the credentials previously entered by the user.
- The IDP STS server provides a security token (containing a set of claims) to the user.
- The user is redirected to the application and the user’s security token is presented to the application and the application opens in the user browser.
In this topology, the AD FS server does not get exposed to the Internet and you can’t federate it with external partners as RP. This is purely for internal use only, WebSSO solution design.
Next post will discuss the next topology – Authentication to UAG Portal via Certificate Based Authentication (Soft Certificate or Smart Card based certificate) and accessing internal claims based application and other types of applications.
UAG and ADFS are Better Together– Strong Authentication
In the previous section we looked at the most common UAG configuration, with user using username and password for authentication to UAG. In this section we are going to explorer the following configuration – user authenticates to UAG Portal via Certificate Based Authentication (Soft Certificate or Smart Card based certificate) and then access internal claims based application and other types of applications.
Smart Card authentication is becoming a major requirement in many industries. In Federal Government very soon it will be a mandatory authentication mechanism for internal and external logical application access.
AD FS configuration in this topology is very similar to previous topology, but with a few very critical differences. To enable Smart Card authentication, the UAG trunk is configured to require certificate authentication. During certificate authentication, the user will use a certificate from his smart card, it will be presented to the UAG server and UAG server will authenticate user based on the certificate content, usually it is done based on the value of Subject Alternative Name extension UPN value. UPN stands for Universal Principal Name, it is e-mail like value and it is enforced by Active Directory to be unique. UAG will read this value from user certificate and map it against Active Directory user account with the same value. All of this is done via Kerberos authentication and nowhere during this process has user provided his username or password.
Figure 4 shows classic design with Microsoft Active Directory (AD) acting as main authentication directory and providing access to the internal applications using Kerberos authentication and providing authentication to the IDP STS.
Figure 4: System Components
So how does user get security tokens from AD FS in this configuration? UAG must be able to authenticate to it on behalf of the user, but user never provided his username and password. It is done via Kerberos Constrained Delegation (KCD). UAG is configured to be able to impersonate authenticated user via KCD and request service ticket from AD and present it to the AD FS server on behalf of the user. AD FS will issue security token to the user and user will be able to authenticate to the claims based application the same way as it was done in the previous topology. Let’s review step-through process again, Figure 5 show us simplified authentication flow.
Figure 5: Authentication Flow
- Remote employee goes to the Forefront UAG portal and authenticates against the AD DS server using Certificate based authentication (Smart Card). They will get access to the UAG portal with published applications based on their security profile.
- When user tries to access claims based application, the application will redirect the web browser request to the AD FS v2 server for user to obtain a security token.
- Depending on the configuration, the AD FS server might show the home realm discovery page to users on which they must choose the organization to which they belong; in this case, it would be Woodgrove Bank, but since this is a WebSSO configuration, the IDP STS will not show home realm discovery page.
- The IDP STS will send back a HTML 401 response message for user to authenticate. Forefront UAG is able to provide a single sign-on (SSO) experience for the user by answering the 401 response with the Kerberos ticket acquired on behalf of the user (KCD).
- The IDP STS server provides a security token (containing a set of claims) to the user.
- The user is redirected to the application and the user’s security token is presented to the application and the application appears.
While this topology increases security of initial authentication, it does lead to some limitations on the back end authentication and limits Single Sign On experience. To provide seamless access to back end applications they must support Kerberos authentication. On top of that, application servers must reside in the same Active Directory Domain as UAG server (obviously that means that UAG must belong to AD domain) and the user account must be in the same Active Directory Forest as UAG server as well. Also, there are requirements on the Domain and Forest Functional level, it must be at least at Windows 2003 level. These requirements put some limitations on the Single Sing On experience. If one of the listed conditions is not satisfied and user tries to access published application, the KCD will not work and he/she will be prompted to provide credentials in the common form of domain\username and password.
Same as in previous topology, the AD FS server does not get exposed to the Internet and you can’t federate it with external partners as RP. This is purely for internal use only, WebSSO solution design.
UAG as AD FS Proxy
In previous topologies (1 and 2) we did not expose AD FS server to the outside users as primary form of authentication. This topology will do this. One of the benefits of using UAG server in combination with AD FS is that it can now act as gateway or proxy server to the internal AD FS server, in fact UAG can now be configured as the relying party with AD FS server and accept SAML token for user authentication.
Figure 6 shows topology with AD FS acting as main authentication directory and providing access to internal claims based applications.
Figure 6: WebSSO System Components
With this configuration UAG trunk is configured to use AD FS for authentication, it passes you all the way to the AD FS server, which challenges you for credentials, in this case it will prompt to provide username and password. AD FS issues security token to the user and it is presented for authentication to the UAG server. UAG server grants access to the UAG portal based on the security token issued from the trusted IDP STS – our internal AD FS server. Figure 7 shows how UAG trunk and published applications configured with different authentication providers.
Figure 7: UAG Trunk Configuration
When user tries to open published application, the user will obtain a new security token from the IDP STS, specific to this application.
Figure 8 shows authentication traffic to access the UAG portal and Figure 9 shows how user will access published claims based applications via UAG portal.
Figure 8: WebSSO Authentication Flow
- The remote user attempts to access Forefront UAG portal. Since the UAG trunk is configured to use AD FS as its authentication provider, the Forefront UAG redirects the web browser request to the AD FS (IdP STS) server to authenticate the user. During this step, the IdP STS server might show the home realm discovery page to user (not shown in this diagram) on which he/she must choose the organization to which they belong; in this case, it would be Woodgrove Bank, but since this is a WebSSO configuration, the IDP STS will not show home realm discovery page. The IdP STS must authenticate the user. Depending on how it is configured, it might present user with AD FS Forms based authentication page or it might prompt with Windows authentication pop-up dialog box. The remote user provides credentials and authenticates using his/her own AD DS credentials.
- After successful authentication IdP STS creates security token with claims and it is transferred to the user.
- User is silently redirected and automatically authenticated to Forefront UAG using the security token created by the IdP STS server. User will see UAG portal with applications that this user is authorized to access. It is important to note, that authorization is done via claims and not via traditional windows security groups. In this configuration UAG did not authenticate the user against AD, it authenticated user solely based on the SAML token, and as such, the authorization decisions must be made based on the content of SAML token. Thankfully, Forefront UAG is smart enough to perform such authorization decisions.
After user authenticated to the portal he might decide to access published application, after all, why access the portal if not using applications?
Figure 9: WebSSO Authentication Flow
- The remote user attempts to access the published claims based application using claims-based authentication in one of two ways, listed below. Regardless of the mechanism, target application will redirect the user to its trusted Resource Provider STS, in our case it is IdP STS.
- By accessing the Forefront UAG portal and then clicking the published application (this is the follow up procedure to the previous diagram)
- Or by accessing the published application directly using the alternate access mapping name (if application was published that way). If this is the case, the preceding steps in the previous diagram might take place as well, but user will not see the UAG portal, he will be taken straight to the published application.
- Forefront UAG redirects the web browser request to the IdP STS server to authenticate the user. Since user is already authenticated to IdP-STS when he authenticated to UAG portal, he will automatically re-authenticate to it with current session cookie.
- IdP STS creates security token with claims for published application and it is transferred to the user.
- User is silently redirected and automatically authenticated to the published site, after which the site appears.
By using UAG as the front end secure access point we are actually able to simplify AD FS infrastructure. In most situations, for Internet facing deployments, AD FS would deploy Federation Proxy server, which authenticates users on behalf of the internal AD FS server. With this configuration UAG server act as the front end gateway to the internal AD FS server and it is publishing AD FS authentication pipeline via its application publishing mechanism.
At this point it would be a good time to mention what type of UAG Portal features are not available if UAG trunk is configured as relying party to AD FS server. The first one is important to mention because it relates to the user password management. When UAG trunk is configured with AD authentication, it is capable to provide the following two important functions for our remote users:
- Password expiration notification. This is configurable on the trunk usually with 7 days threshold. If user password is about to expire, UAG will notify the user about it and allow to change it to a new password.
- Password change. After user authenticated to the UAG portal, he can always change password via this function. So if remote users are never come on site and they have no way to change their AD passwords via normal mechanism, then this is pretty much the only mechanism for self-password management.
With UAG trunk configured as relying party to AD FS, it never authenticates to AD. AD FS server authenticates user to AD and provides SAML token to UAG for authentication. UAG portal will never know if user password is about to expire and it is not capable to change user passwords because it is not configured with AD as authentication provider. Unfortunately, none of the password management functions provide via AD FS authentication, all it does, is authenticating the user. It will not notify the user about pending password expiration, nor does it provide the mechanism for password change. This is important limitation as it might affect overall design of your solution. If you must provide password management to your users, then you must publish UAG portal with AD as primary authentication provider.
There are other UAG features that are not available with AD FS authentication, here is a short list:
- UAG supports only WS-Fed Passive profile
- No Rich Applications publishing with AD FS authentication
- Impact on Office Applications
- Cannot publish applications installed on the AD FS 2.0 server
- No HTTP to HTTPS redirection
- No mobile device access on federated trunks
Strong AuthN to Cloud Based Applications
In this section we will discuss a solution that provides the following functionality: You what to require your company external users to use strong AuthN when they access 3rd party trusted claims based applications. These applications can be hosted in the Cloud or by Partner organization.
The description of this topology is a mouthful, but that is exactly what this topology provides to us. It is really an extension of the second topology with addition of federated Resource Provider components. Figure 10 shows this topology.
In many situations you want to allow your remote users to be able to access claims based applications published by your business partners. So the critical question is how do you want to authenticate your remote users against IDP STS? Business partner would usually have RP STS which will issue security tokens for application access. Your user identity does not come from RP site of the equation; it comes from your side. If you want to increase the security, and in the current day and age it is becoming a requirement, your remote users must use smart cards before they can gain access to the IDP STS and receive their initial security token.
First, remote user will try to access partner application which will redirect them via their RP STS back the IDP STS Federation Service. IDP STS external URL is published via UAG and it will require smart card authentication. User authenticates to UAG, receives their security token from internal IDP STS and redirects it back to RP STS and then gains access to the partner application.
Figure 10: System Components
Figure 11 shows authentication traffic to for this configuration.
Figure 11: Authentication Flow
- First, remote user will try to access application published by the Partner organization or by the Cloud Application provider.
- Application will redirect user browser to its own STS (RP-STS). RP-STS will need to perform a home realm discovery. At this time user will be automatically or manually redirected to his own IdP-STS.
- Since in this situation, the IdP-STS is published via UAG on the a trunk that requires certificate authentication, the user will be prompted to authenticate with his Smart Card. The authentication will be done against his corporate AD.
- When UAG authenticates the user, it will use Kerberos Constrained Delegation to authenticate to the IdP-STS, and those providing SSO experience to the user. IdP-STS will authenticate the user and will issue Security token for RP-STS.
- User browser will receive the token from IdP-STS and post it to the RP-STS.
- Finally, RP-STS will take token issued by IdP-STS, it will evaluate it content and based on its own rules, will create its own security token. Claims in this token might be the same as what was issued by IdP-STS or they can be transformed according to specific business rules. User browser will receive the final token from RP-STS and will post it to the target application. Application will authenticate the user and proceed with its logic.
As we can see, this configuration topology provides a powerful way to increase remote user security and it did not require any type of special modifications on the part of the Resource Provider organization. For all they care, the initial authentication by the end user was done via any type of authentication mechanism. It gives a powerful and flexible way to security managers to increase their organization security posture and the same time provide access to remote applications over which they have no direct control.
Publishing Non-Claims Based Applications
In article “UAG and AD FS are Better Together – UAG as AD FS Proxy” we explored how user authenticates to UAG portal via claims based authentication and then accesses claims based application published via UAG portal. But what if published application does not support claims based authentication, after all how many applications out there that do? Fortunately, UAG is capable to publish and provide SSO experience for non-claims based applications as well. The caveat here is that they must support Kerberos authentication. If you remember this “UAG and ADFS are Better Together– Strong Authentication” topology where we provided access with strong authentication, we configured KCD authentication between UAG and AD FS server. In this topology the configuration is slightly different but concept is the same. Instead of doing KCD between UAG and AD FS, we’ll need to configure KCD between UAG and the target application.
UAG is smart enough to transition from the claims based authentication and request Kerberos ticket from AD Domain Controller on behalf of the user. During application configuration you’ll need to specify what claim you’d like to use as a leading value to get the Kerberos ticket. UPN is a good choice. Also, the proper SPN must be configured in AD for the target application.
Figure 12 shows main aspects of this configuration and Figure 13 provides high level authentication steps of how this works. It is very similar to the previous configurations, just in slightly different order.
Figure 12: WebSSO Components
- First, user must authenticate to the portal with SAML token, this is done via authentication to the backend AD FS server.
- When user tries to access published application that was configured with Kerberos Authentication, the UAG server will contact AD Domain Controller and will get Kerberos Service ticket for the target application. It will use the claim value that was configured with this application in its request to Domain Controller.
- Then UAG will send Kerberos ticket to the target application. Application will use the Kerberos ticket for authentication and authorization decision.
- If authentication was successful target application will allow access to the end user.
Figure 13: WebSSO Authentication flow
This configuration has similar constraints as was discussed in topology with Smart Card authentication, they relate to the Kerberos constraints. In this configuration application servers must reside in the same Active Directory Domain as UAG server (obviously that means that UAG must belong to AD domain) and the user account must be in the same Active Directory Forest as UAG server as well. Also, there are requirements on the Domain and Forest Functional level, it must be at least at Windows 2003 level.
Publishing Applications to Partner Organizations
In this scenario, our partner organization users access claims based applications published by our organization UAG servers. The partner users provide security tokens issued by the partner controlled Identity Provider to our AD FS v2 published by the UAG server. This configuration is the most common federated access scenario, and UAG works very nicely to make it all happen.
The ultimate goal of such configuration is to provide a SSO experience to the end user and never ask them for additional credentials or any type of questions. There are two main areas that must be properly configured to accommodate SSO. The first one is part of the partner organization configuration. Their IdP must be able to authenticate the user on their internal network via SSO. This is easily done if IdP is using AD FSv2. As part of the same AD Forest, it will authenticate internal users via Windows Integrated Authentication and will issue the required security tokens. The second part in this configuration is to configure Home Realm discovery. RP-STS residing on our network (woodgrovebank.com) is probably acting as IdP for internal users, or it might have more Federated trusts with other IdPs. The proper configuration of Home realm discovery is important in Federated configurations so that users are not confused where they need to authenticate and that they might not need to see other partners in your organization. Home realm discovery can be configured via multiple ways and is a topic of its own. We will cover it sometime in future updates to this paper or via a separate article.
Figure 14 shows the overall topology for federated application publishing. If you are familiar with all previous topologies, then you can see how this will work, as it is pretty much an extension on all the previous configurations. Let’s take a look via Figure 15 at the high level authentication flow.
Figure 14: Federated WebSSO Components
- First, the remote user will try to access the application published via the UAG server. Since the application is configured to work over claims-based authentication, it will redirect the browser to its RP-STS.
- RP-STS can be published on the same UAG trunk as our application. This trunk must not use internal AD for authentication. It must be configured as AD FS proxy trunk with RP-STS as the AD FS server behind it – i.e. it must be acting as a relying party. The user will contact RP-STS to get the security token for our target application. This is when Home Realm discovery takes place. If Home Realm Discovery is not configured to automatically redirect this user to his own IdP, then he/she will be prompted to choose his IdP from a list of configured trusted IdPs.
- During this step, the browser is redirected to his IdP, and it will try to request a security token for RP-STS. IdP-STS and RP-STS have a trust relationship, and, based on the conditions of this relationship, the IdP-STS will issue a security token to the user.
- This token will be posted back to the RP-STS, where it will be evaluated and based on the configured rules, and transformed into a new security token with a new set of claims suitable for consumption by the target application.
- The token generated by the RP-STS is redirected back to the user computer, and then, in steps 6 and 7, this token is posted back to the target application. The application will make its authentication and authorization decisions based on the claims presented in the token.
Figure 15: Federated WebSSO Authentication Flow
This topology is an extension of the third topology we discussed in this paper, (Authentication to UAG Portal via Claims Based Authentication and accessing internal claims based application,) and all of the specific configuration related to the UAG and AD FS server are generally the same as in that configuration. The main differences are related to the more complicated Home Realm Discovery configuration and configuration of the partner IdP-STS.
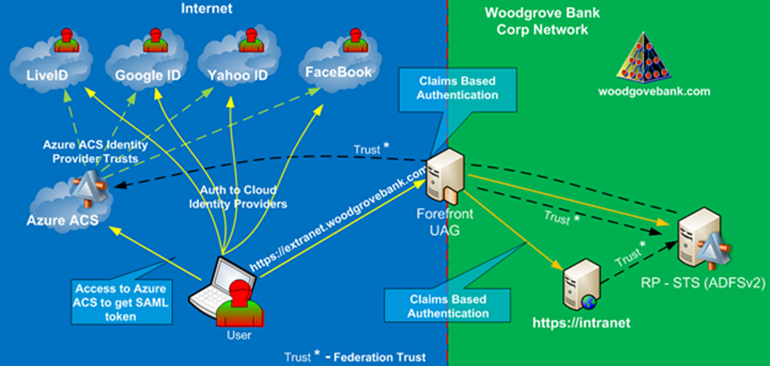
Authentication via Azure ACS
This section discussing how it is possible to publish applications to Internet based users who authenticate to the UAG via one of the Internet Cloud Identity Providers, such as LiveID, Google, Yahoo or Facebook. The Windows Azure ACS acts as IdP-STS in this configuration topology.
This is essentially the same as what we discussed in the previous configuration, where we published applications to partner organizations. The key difference here is that we do not actually have a specific individual organization. In this configuration, we are able to provide access to our applications to anyone who already has an identity at one of the big Cloud Identity providers – Microsoft LiveID, Google, Yahoo and Facebook. This accounts for millions of users.
The Microsoft Cloud development platform, Azure, provides this very unique capability via Azure Access Control Services. Azure ACS is configured to use these four identity providers as a potential authentication source. Very minimum configuration is required. Azure ACS must be configured as a trusted Identity provider with our internal RP-STS. From there on, the authentication is very similar to Federated WebSSO.
After the user tries to access the published application, he will be redirected to the RP-STS. Home Realm Discovery will be done at this point, and the user will be redirected to the Identity Provider, in this case Azure ACS. Depending on how Azure ACS is configured, it will redirect the user to one of the Cloud providers or it will give the user the option to choose one of them. The user will authenticate to the Cloud Identity provider and will be redirected back to Azure ACS, which, in turn, will create a SAML security token, provide it to the user, and from there on it will be posted back to RP-STS, transformed, and provided to the target application. Figure 16 shows the high level configuration for this topology.
Figure 16: Azure ACS in Federated WebSSO
Designing UAG and AD FS Solution
Now, since we are armed with knowledge of different configuration options, we can put all of them to use and see how we can apply them to real life situations. Before we do this, we need to revisit some critical technical requirements that exist with UAG and ADFS v2.
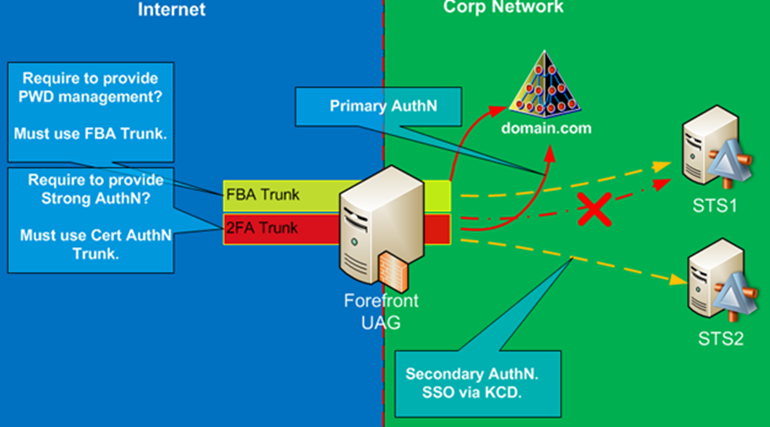
- The UAG server can use the same AD FS v2 Federation Service URL only in one UAG trunk. This constraint is very important to understand because it is one of the critical elements that will affect your design.
- Based on the previous requirement, if your configuration requires multiple UAG trunks with AD FS v2 support, and we will examine shortly why this might be the case, you will need to implement a separate AD FS v2 server for each UAG trunk.
- UAG can provide Kerberos Constrained Delegation (KCD), but with the following constraints:
- The UAG server must be in the same AD domain as the application server it is trying to access;
- The User Account used to authenticate to the UAG server (the one we need to use KCD for) must be in the same AD Forest as the UAG server. If the user comes from a trusted AD Forest, the KCD will not work.
While designing your solution, you will have to gather a lot of requirements and understand the customer’s situation. Some requirements will force you into certain design topologies, and it is important to answer them at the beginning of the design process. There are at least three main questions that you have to answer when designing your UAG/ADFS access solution. The answers to these questions will direct you into a certain design topology or might require a combination.
The first question relates to password management. If you have a requirement to provide password management capabilities to remote users, -i.e. password change and notification of expiring password, you must use a UAG trunk that uses AD as the primary authentication provider. This type of trunk will authenticate you before providing access to any published applications. Access to claims based applications will be done via a secondary authentication to the back end published AD FS v2 server. This is the first topology that we discussed in the first part of this paper. Figure 17 shows this configuration.
Figure 17: UAG with One Trunk and dedicated AD FS in each Trunk
The second question relates to strong authentication, i.e. Smart Card based authentication. If there is a requirement to provide Strong Authentication, then your remote access solution must have topology #2, with UAG trunk configured for Smart Card authentication against the Active Directory and the AD FS server configured as an authentication provider for the claims based application. Anytime there is a requirement to use Smart Card authentication on the UAG portal, it will consume at least one AD FS Federation Service. Since we cannot use the same trunk to provide authentication via AD UserID/Password and Strong Authentication, the configuration will have at least two UAG trunks. Figure 18 shows this configuration.
Figure 18: UAG with Two Trunks and dedicated AD FS in each Trunk
The third question relates to the federation requirements with other companies. We need to identify if there is a federation requirement with external partners, specifically with IDP partners, where your company provides application resource for their use. If there is none, then our solution encompasses topology #1 and/or #2. If you must support federation as RP STS, then it complicates things. UAG trunks used for FBA or Smart Card authentication will consume their AD FS Federation Services, and it cannot be used by another trunk on the same UAG server.
We must implement yet another AD FS Federation Service on the internal network. If you need to satisfy all three requirements, you will need to have at least three UAG trunks, each with its own dedicated AD FS v2 server. Figure 19 shows this configuration.
Figure 19: UAG with Three Trunks and dedicated AD FS in each Trunk
As you see in Figure 3, this is not a simple solution anymore. While we can use the same UAG server to publish all of these services and all kinds of applications, we must implement three separate AD FS services. However, this is not the end of the complications. There are still some critical design decisions that you must make. What is the ultimate goal of this solution? Yes, the goal is to publish applications to the end users. And what type of applications are we trying to publish via UAG/ADFS configuration? We are trying to publish claims based applications. Let’s think for a moment about configuration requirements for claims-based application. The first and foremost requirement is that it must be configured with a trusted Security Token Service. It must be able to accept security tokens from trusted STS for user authentication.
How would we need to configure the claims-based application with multiple AD FS v2 servers and multiple UAG trunks? The first logical way to look at it is by creating trusts between the target application and each STS. As shown in Figure 20, in such configuration each trunk will have its own AD FS server which will be able to issue security tokens to the application. The problem with this approach resides with Home Realm Discovery. If we configure the application to trust multiple STSs, we have to make some type of determination at the application level of where the user must authenticate to get the valid security token. We are taking Home Realm Discovery out of the AD FS realm and trying to do it at the application level. While theoretically it is possible, the reality is that applications are not designed to do Home Realm Discovery. The underlying Windows Identity Foundation service must be extended to provide this functionality, which is not very easy to do and, in most situations, is not the best practice. The goal behind claims based authentication is to simplify authentication and simplify the application developer’s life, thus outsourcing authentication related Home Realm Discovery functions to the services designed for this purpose. The bottom line is that setting the application with multiple STSs is not recommended, and it is not the best practice.
Figure 20: Application with multiple RP-STS
The other common way to configure claims-based application is with one STS. Usually it will be designated as the Resource Provider role (RP-STS) and let RP-STS issue all security tokens for this application. RP-STS will be required to route user requests destined for other Identity providers. In our configuration, one of the AD FSv2 servers will be acting in this role. Which one should it be? The STS published via federated UAG trunk, (i.e. with UAG acting as AD FS proxy,) is the right choice for RP-STS. The configuration is shown in Figure 21.
Figure 21: Application with dedicated RP-STS
This is a complex solution, but if you must have at least two UAG trunks with support for claims-based applications, this is the only viable choice to publish them.
In the next post we will take a look at a specific real world example of how UAG and AD FS can be used to publish applications.
Example of a real Solution
In prior sections we reviewed different topologies and discussed some of the techniques on how to integrate these topologies together. In this section we’ll take a look at real example of a production implementation.
The solution very similar to the following design has been implemented by one of the large enterprise companies. We will review it here in some detail. Every real world implementation is based on some type of specific requirements that the customer would like to satisfy. The solution is called “Application Gateway” or simply “Gateway”. The following are the main requirements that this solution must satisfy:
- Provide a secure infrastructure solution that can be accessed by users over the Internet.
- Provide an application portal to host applications for access by both internal and external users.
- Allow external users to create accounts.
- Allow external users to change their passwords.
- Provide external users with self-service password reset functionality.
- Allow internal users to leverage their current existing credentials for gaining access to the resources in this solution.
- Federated access to published applications by partner users.
- The solution must be secure, implemented in the DMZ environment, and ideally without Windows trusts between this solution environment and internal AD.
I just listed the main ones, but there are many more specific requirements. Those are not necessarily dictating the overall solution architecture.
The following software components are part of the solution, with Figure 22 showing how they relate to each other:
- FIM 2010 R2 – All IDM related functions
- Self-registration for external users
- SSPR for external users
- Group Management for application access AuthZ
- Approval Workflows for user creation
- UAG SP1 – External and Internal entry into the application hosting environment
- AD FS v2 – Authentication into the environment
- For external users access to SAML apps
- For internal users SSO to Gateway and access to SAML Apps
- SCOM/ACS – Monitoring and Audit
- AD – Directory Services
Figure 22: Solution Components
UAG Trunk Design in this solution will have at least three trunks on each UAG server, as shown in Figure 23.
- The first trunk will publish Anonymous applications. This trunk will be configured without any authentication requirements. The following are primary applications that will be published via this trunk:
- Initial landing page for users with menu selection of different tasks
- Self Service Password Reset application
- Self-User Registration application
- The second trunk will publish a portal for external users with password change function
- This trunk will use AD for primary authentication to the portal
- Will use AD FS as secondary for claims-enabled apps
- The third trunk will publish a portal for users authenticating via SAML (Federated)
- This trunk will use AD FS as the primary authentication to the portal
- It will be configured as a relaying party with RP-STS
Figure 23: UAG Trunks
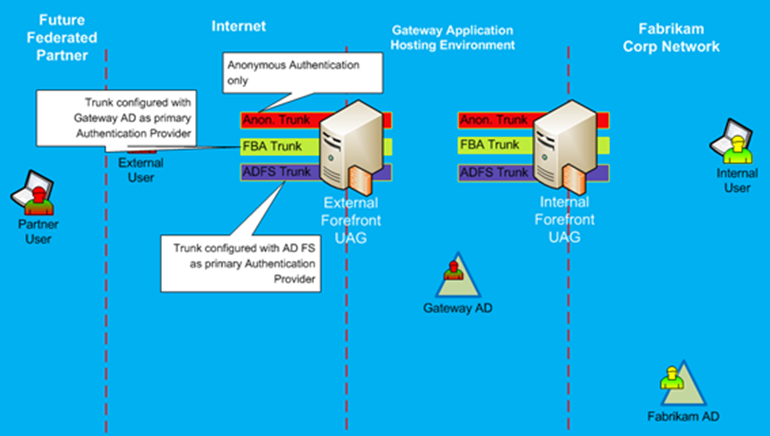
Figure 24 shows Federation configuration for this solution. It will have at least three AD FS Farms:
- The first farm will act as resource provider, and it will be configured with all applications in the Gateway application environment. All claims-enabled applications will trust this STS. In Figure 23, it is shown as RP-STS (fs2.fabrikam.com). As you can see, both UAG servers, specifically ADFS configured trunks, are some of the applications that are configured as relying parties with this RP-STS.
- The second AD FS server farm will provide SAML tokens to external users with accounts in the Gateway Active Directory. It will act as an identity provider to external users who have accounts in the Gateway AD. This STS is shown as IdP-STS (fs1.fabrikam.com). This STS will not be accessed via UAG as by means of UAG proxy. Instead it will be published on the FBA trunk as a secondary authentication provider.
- The third AD FS server farm will provide SAML tokens to internal users with accounts in Corporate Fabrikam AD. It will act as an identity provider to internal users. This STS is shown as IdP-STS (fs3.fabrikam.com). This STS is not published via UAG. In fact, it is providing Federated WebSSO to the RP-STS, so that internal Fabrikam users will be able to authenticate into the Gateway environment without being required to have a known UserID/Password in the Gateway AD.
Figure 24: Federation Design
At this point, we need to review a very important technical requirement that must be satisfied for this solution to work. Internet facing UAG and internally exposed UAG must be resolved via the same DNS name. They must be identical. In other words, if an Internet based client types in the browser the name for this portal as portal.fabrikam.com, it should resolve to the external UAG IP address. At the same time, if internal user, using a computer on the corporate network is using the same URL, it should be resolved to the internal UAG server IP address. Why is this the case? It actually has nothing to do with UAG. This requirement comes from AD FS – the federation service URL always stays the same. In our example, if the client needs to get a SAML token from the fs2.fabrikam.com AD FS server, it must be able to resolve this URL and connect to it via that URL. Since this FS service is published via two different UAG servers, both sides of the users must be able access it via the same URL.
The easiest and most common way to satisfy this requirement is by having “split-brain” or dual zone DNS design. Basically, companies would have two different zones with the same name, one exposed to the Internet and one that is only internal. Figure 25 gives a visual demonstration of this requirement.
Figure 25: Split brain dual zone DNS design
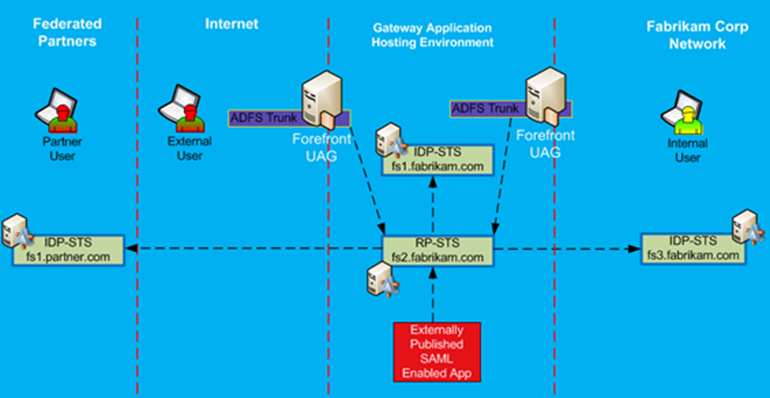
Let’s review how different users would authenticate into the Gateway and access published applications. First, we will start with internally based users. Figure 26 provides a high level flow of how internal users will authenticate to the internal UAG server. For internal users whose domain was federated with Gateway, they will use the ADFS trunk as their primary portal. When they try to authenticate, they will be using Federated WebSSO, with first step (1a) accessing RP-STS and performing a home realm discovery, which will redirect them to their internal IDP-STS in step 1b, where they get their initial SAML token, which will be provided back to RP-STS (step 1c). RP-STS will issue the final token, which the client will provide to the ADFS trunk (step 1d), and the user is authenticated to the portal.
Figure 26: Internal user authentication to UAG
After successful authentication, the user will see a list of applications published to him via the AD FS trunk. The authorization to see these applications must be done via contents of the claims. Using normal security groups from Gateway AD will no longer work because the internal user actually does not use Gateway AD for authentication to the portal.
There are two types of applications that are supported via AD FS enabled trunks: Kerberos Applications and Claims-enabled applications.
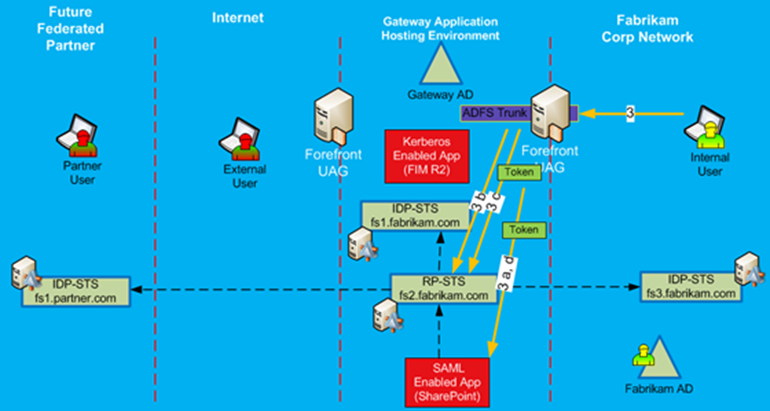
In this solution, FIM 2010 R2 must be published to the internal users so they can get into the FIM 2010 R2 portal and perform administrative tasks, such as approve or deny external user account requests. FIM R2 is not a claims-enabled application, but it is a Kerberos based application and it can be published via AD FS enabled trunk by using Kerberos Constrained Delegation. Of course for this to work, the Gateway AD must have a shadow account for internal users. FIM R2 will actually help with creating shadow accounts. It is configured to synchronize internal Fabrikam AD user accounts into the Gateway AD, thus creating a shadow account for internal users. It will not synchronize user passwords into Gateway AD.
Figure 27: Internal user accessing Kerberos Applications
Internal users will be able to access FIM R2 via SSO experience and perform their work as needed. Figure 6 shows the basic authentication step for Kerberos based application. In the future, this solution will be able to publish other Kerberos based applications, and they will be accessed in the same way as FIM 2010 R2. They will require proper SPN configuration and Gateway AD, but users will already have shadow accounts.
The other type of applications that can be published via AD FS enabled trunks are claims-based applications. These are easy and straight forward to publish and access via AD FS trunk. Figure 28 provides a high level authentication flow for internal users.
The interesting part in this authentication flow and what is different from the original authentication to the portal itself is the fact that the client does not need to get another security token from its internal IdP-STS. Since he is already authenticated to the portal, after the client tries to access the published application, the client browser will only need to request a new security token from RP-STS, specific for this application, as it shown in Figure 28.
Figure 28: Internal user accessing claims applications
Finally, we can examine authentication flow and application access by external users. There will be two types of external users: users with accounts registered in the Gateway AD for which they know their passwords and federated users, whose identity belongs to some other organization. Each user type will have to use different trunks for authentication.
External users with accounts in Gateway AD will be accessing it by using a UAG trunk with Gateway AD as the primary authentication provider. The primary reason for this configuration is to allow these users to change their passwords and to notify them when their password is about to expire. Trunks that use AD FS as the primary authentication provider do not provide password management functions.
Federated external users will access the portal via UAG trunks with the AD FS server as the primary authentication provider. While these users are important to the future of this solution, the current primary user base will consist of external users with accounts in Gateway AD, and, for this reason, Figure 29 shows the authentication flow and access to applications for these types of users only.
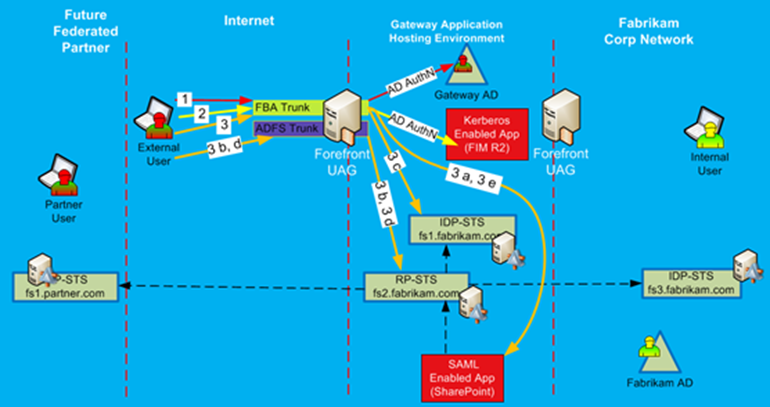
First, the user will need to authenticate into the portal, which will be done via UAG forms based authentication with Gateway AD account. After successful authentication into the portal, the user will be presented with a list of applications, which he/she has been authorized to access. The authorization is based on the AD group membership. The authentication flow to the application will depend on the application type.
Non-claims enabled applications are actually very straightforward. For example, FIM 2010 R2 will be published to external users by using SSO function of the UAG trunks, and it will use the same authentication provider as for the trunk itself. Users will access such applications by utilizing their AD credentials, with UAG taking care of this authentication behind the scenes and without any special type of configuration requirements. This flow is shown as step 2 to Kerberos enabled applications.
Authentication to claims-enabled applications will be a bit more complex. Figure 29 shows it with step 3 flow. The application is published via the FBA trunk portal, and the user will try to access it via that portal. With step 3a, it will contact the application and learn that the application trusts RP-STS. RP-STS is not published via FBA trunk. It is published via ADFS Trunk, a different trunk on the UAG server. In step 3b, the user’s browser will be redirected to the RP-STS to get the token for the target application. Theoretically, we could issue a SAML token at this point in time, but since RP-STS is not published via an FBA Trunk, we will not be able to provide SSO experience to the end user. If we would end the process here, the user would be required to authenticate to RP-STS. Since there is no SSO for this user on the ADFS trunk, he/she will be prompted for credentials. Instead, the Home Realm Discovery will happen, and the user will be redirected to the IdP-STS (fs1.fabrikam.com). IdP-STS is published on the FBA trunk, and it is configured with SSO authentication via Gateway AD. The user is already authenticated to the FBA trunk and via step 3c will authenticate to the IdP-STS and receive security token. This token will be posted back to the RP-STS in step 3d, which will be transformed into a new token, suitable for the target application. It will be provided back to the client computer and posted to the application via FBA trunk in step 3e. The application will authenticate the user and open in the user’s browser.
Figure 29: External User Authentication and Application Access
It is not the most straightforward authentication experience, but as discussed earlier in this paper, configuration of claims-based applications with multiple UAG trunks requires separation between Resource Provider STS and Identity provider STS. Otherwise it will not be published via different UAG trunks.
Authentication of a federated user via an external UAG server is done the same way. It is for internal Fabrikam users, straight forward federated WebSSO.
Things to know about this design:
During the implementation of this solution, we discovered a few restrictions in AD FS that would not be very obvious if we used only one UAG server. However with dual implementation and especially with identical name spaces on Internet and Intranet, we ran into some minor constraints. Fortunately, fairly easy workaround were quickly identified to bypass them.
The first constraint is related to the certificate usage on AD FS. It will not allow the use of the same certificate (certificate with the same hash) on multiple relying parties. Why is this a problem? Since we have the identical name space on the internal network and external network, originally we tried to save on costs and use the same wild card certificate (*.fabrikam.com) on external UAG and internal UAG servers. UAG servers will work just fine with the same cert, but when time came to set them up as relying parties on the AD FS RP-STS server, we encountered a problem. AD FS did not allow the creation of the second relying party with a certificate whose hash had already been used by another relying party. The simple solution to get around this problem is to issue two different wild card certificates, one for internal UAG and one for external UAG. Usually these certificates must be trusted by Internet clients, so you would need to get them from one of the commercial certificate providers, and it will double your cost.
The second constraint is related to the naming of the ADFS Trunks on external and internal UAG servers and the potential conflict with RP-STS Federation Services for each relying party. During ADFS trunk configuration on the UAG server, it is most logical to configure the public URL for the trunk to match the URL of the published Federation server. By default, you would probably create the ADFS trunk for fs2.fabrikam.com AD FS with the same URL, i.e. it will be fs2.fabrikam.com. Then you would proceed to configure AD FS with the UAG relying party, which will configure it with the Federation Service URL as fs2.fabrikam.com. So far so good, we have no issues. Now, we proceed with the configuration of the second UAG server, where we create the UAG trunk for internal users, with the same URL, to match RP-STS, ie, fs2.fabrikam.com. This is done without any issues on the UAG server. The second step in configuration will be the creation of the relying party trust on the AD FS server. AD FS will not allow you to create the relying party trust to the second UAG server. This is because it is using the same URL as the first one, and AD FS will not allow two relaying parties with the same URL. Fortunately, there is a workaround for this as well. All you need to do is to configure each ADFS trunk with its own unique URL, different from the RP-STS URL. For example, the external UAG AD FS Trunk can be configured with the following URL for its public name: fs2e.fabrikam.com, and internal UAG AD FS trunk can be configured with the following URL for its public name: fs2i.fabrikam.com. When configuring each UAG server with RP-STS, they will appear as different relying parties, and AD FS will be happy. One thing to remember is to make sure that DNS is configured to resolve fs2.fabrikam.com to each respective UAG trunk, i.e. it needs to point to the same IP address as its internal or external public trunks URLs.
Thanks!





















Hi Dimitri, great post.
I have an ADFS / UAG setup question which I need a bit of advise with. I’ve posted the question on the UAG forum. Any chance you could take a look? Any advise is greatly received.
Many thanks
Mark
LikeLike
Hi Mark, what is the question?
LikeLike
Hi Dmitrii,
the post is here:
http://social.technet.microsoft.com/Forums/en-US/forefrontedgeiag/thread/eb7b4fd1-2b2f-4df5-ba62-7118ff9d9666
Thanks for your help.
Mark
LikeLike
based on your description it should work. The same trunk on UAG can only publish apps with the same base url. So if your trunk is portal.contoso.com, then any apps that require its own unique host name must be under the same base url, ie app1.contoso.com, app2.contoso.com etc.
LikeLike
Hi,
I have a question? We are trying to get UAG to work with multiple ADFS v2 farms. Meaning that the ADFS v2 farms are in other non-trusted domains from the UAG domain. Or is there a way to use ADFS v2 as a proxy with UAG to authenticate multi ADFS v2 farms?
Have someone done this before, as we are not getting it to work?
Kind regards
LikeLike
I have not tried it, but you can try to use FBA authN on the ADFS and provide credentials from UAG, like you’d provide it to any other FBA authN application.
LikeLike
Can you provide configuaration details for the last senarios…its quite complicated
I would greatly appreciate
Thanks
KR
LikeLike
Hi Dimitri,
In figure 12 step 1, I assume that a remote IdP (such as is used in Figure 8) can be used to authenticate the user? The reason is, we have an internal IdP that provides login services including 2FA and we would like to use that. Then in step 2, we would provide the user’s AD upn as the claim value. Would that work?
Also, in figure 12, can we provide NTLM credentials to the application instead of Kerberos?
Thanks!
– Bill
LikeLike
You can use remote IdP as long as it is federated with ADFS that is configured with UAG. The Kerberos is required for constrained delegation. NTLM would prompt user for credentials.
LikeLike
Hi Dimitrii,
first of all – Great Work putting this together! Thank you for this, I found many interesting details…
I have one question, which relates to publishing OWA for external clients and providing SSO with ADFS 2.0. The questions relates to the trunk of the UAG. Should the trunk be configured as a Portal or as a web service (Active Directory Federation)? I assume that it should be a Portal trunk, but I read somewhere, that applications, which are not claim-aware as OWA 2013 should be published on a web service trunk in order to work….
Many thanks for your reply. I will follow also your next posts…
Thanks and Regards,
Stoyan
LikeLike
Hey Dmitrii. For starters, very very nice information. These things are quite complex and it’s awseome some “real world” information is shared. I’m kinda strugging with setup a bit similar (but smaller).
I’m using UAG to publish a claims application, its RP-STS and a IP-STS (with it’s own AD). For that i’m using a FBA trunk (with two authentication servers). The weird thing is that I’m not being faced with the HRD page. If I log on using the IP-STS AD credentials, it seems it uses these to log on to the RP-STS directly (yes there’s an AD trust as well…). If I use a smartlink on the other hand all goes fine.
Any idea what I can do to make HRD appear? Or am I required to create a separate trunk (claims/anonymous) for the RP-STS?
Thanks!
LikeLike